Pwn the WIZ connected
Once again, let's spend some money on Amazon....
Once again, let's spend some money on Amazon.
1. The WIZ lightbulb (TAOlight)

WIZ Connected Wi-Fi Lighting (20 euros)
Once delivered, I put the light in its socket and I download the WIZ application.
I set the connection between my Wi-Fi and the device using an android smartphone.
Stay relax light goes on.
Everything is fine. Work as expected. The light is operational.
1.1 The teardown
Pretty simple. Remove the cup and the LEDs PCB.

No tool required.
Second step: Let's remove the two little screws and the envelope:

First time I see this cooler solution...interesting :-)
And now, we have full access to the electronic part:
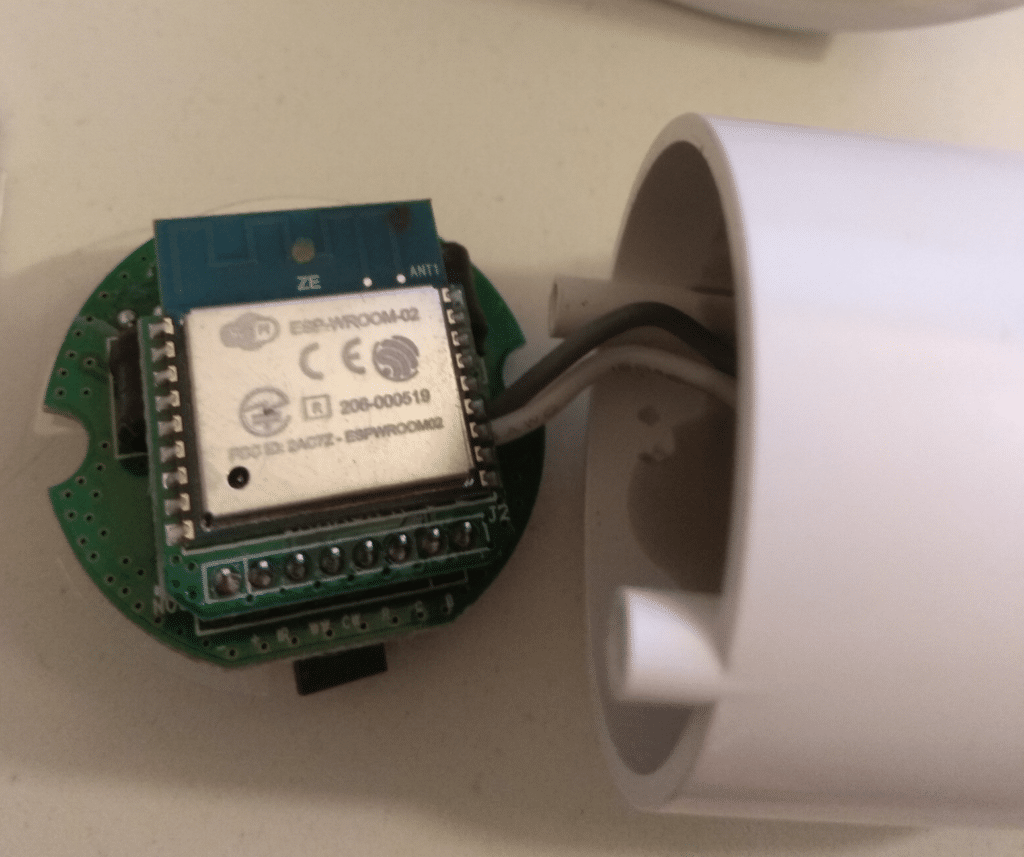
The module is EPS-WROOM-02, pretty standard for someone which have already worked with ESP8266.
SDK, tools and documentation are available here.
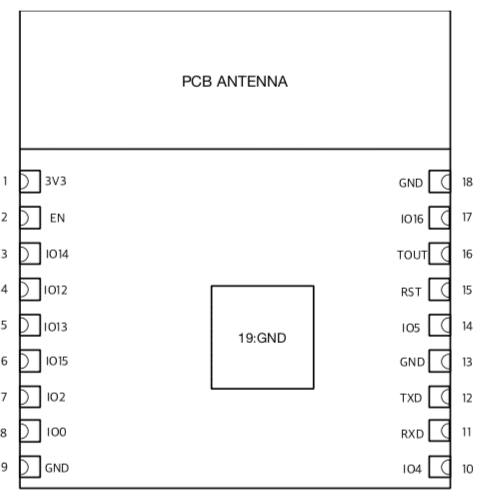
ESP-WROOM-02 Pinout (Front view)
So, fast an easy teardown.
1.2 The setup
Sh**ty device, sh**ty setup. Let's solder some flying wires:
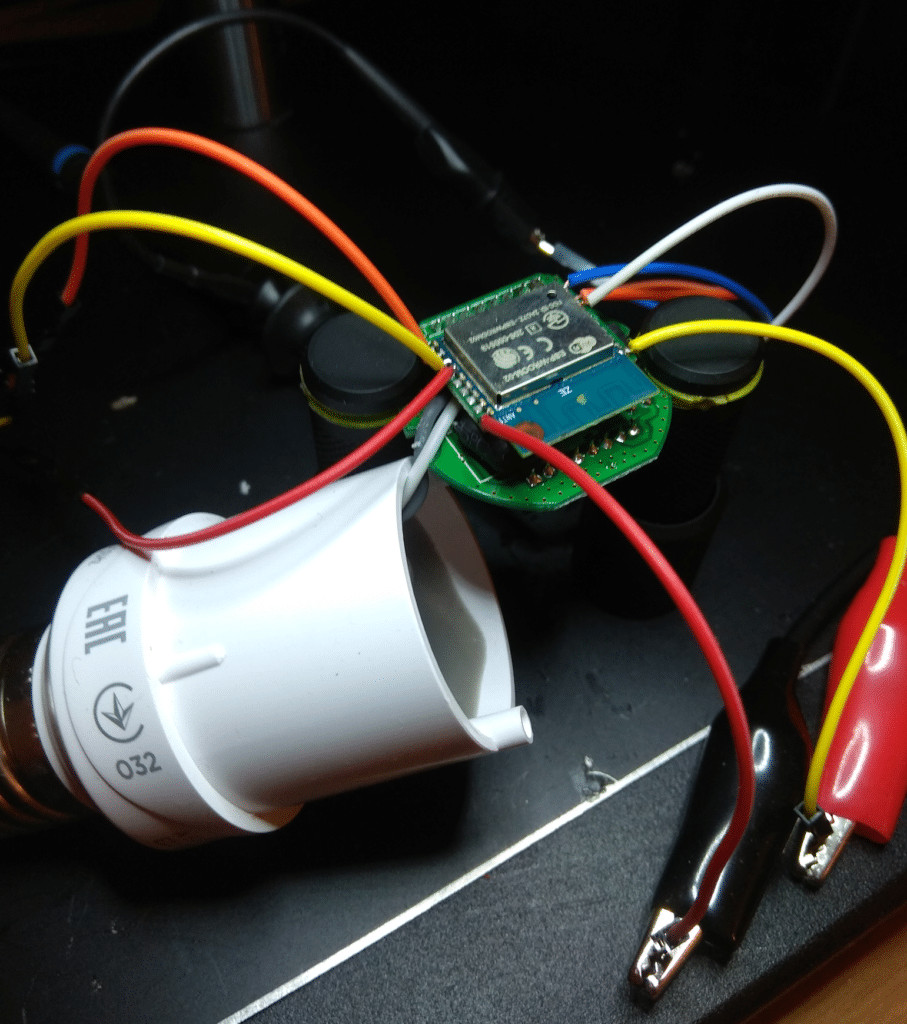
Not my cleanest work, I have to admit
Pins 1 and 18 are connected to the supply voltage 3.3V via crocodile clips. Pins 11,12,13 are the UART connection. UART TX is also present on IO2 (not useful).
Here a relevant schematic to clarify:
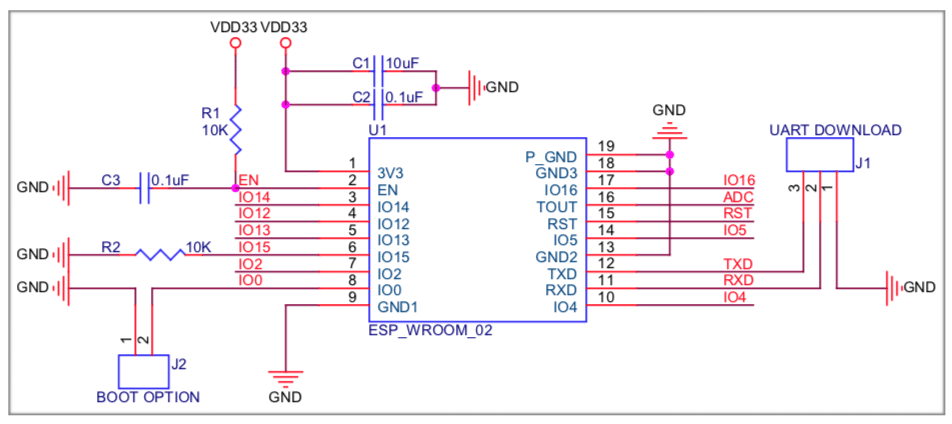
ESP-WROOM-02 schematic
1.3 Dumping the firmware
Once IO0 is grounded and voltage ON, the device starts in UART download mode:
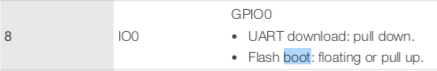
From the datasheet
Dumping the firmware is straightforward:
esptool.py -p /dev/ttyUSB0 -b 460800 read_flash 0 0x200000 flash_contents.bin
Connecting…
Detecting chip type… ESP8266
Chip is ESP8266EX
Features: WiFi
Uploading stub…
Running stub…
Stub running…
Changing baud rate to 460800
Changed.
2097152 (100 %)
2097152 (100 %)
Read 2097152 bytes at 0x0 in 55.1 seconds (304.3 kbit/s)…
Hard resetting via RTS pin…
1.4 Vulnerability n*1: Plaintext User Wi-Fi credentials stored in Flash Memory
Classic on ESP8266 based devices.
ESP8266 does not support flash encryption. The SDK does not provide security features to try to obfuscate at least some private user data.
The SSID and Password are stored four times (the application firmware is duplicated).
1.5 Vulnerability n*2: Firmware can be reflashed
The firmware consist on three stages. Integrity of each stage is checked by one checksum byte. No write protection, no secure boot (ESP8266 does not support this feature).
If I have time, I will upload a little POC (my fault here).
1.6 Vulnerability n*3: Wi-Fi credentials printed on UART
UART log is available by attaching the COM port to a terminal for example Coolterm (74880 8N1). As usual, this baudrate is weird due to the 26MHz Quartz used by the ESP8266.
Funny to see your SSID and your password popping the shell when you are configuring the device:
scandone
TYPE: ESPTOUCH
T|PHONE MAC: 00 ec 0a 72 f0 44
T|AP MAC : 7c ff 4d 4c 5c 8b
T|pswd: 22684319688241754824
T|ssid: KabelBox-0570
scandone
state: 0 -> 2 (b0)
state: 2 -> 3 (0)
state: 3 -> 5 (10)
add 0
aid 6
pm open phy_2,type:2 0 0
cnt
connected with KabelBox-0570, channel 6
dhcp client start…
Of course, as an attacker, I will not use that but it gives an idea about how the product was designed by developers with a strong security in mind.
1.7 Conclusion
WIZ provides the same level of security than the Tuya Light bulbs or LIFX.
Nevertheless, the new thing here is the possibility to obtain secret data and to modify the firmware without destroying the device. The device remains untouched after the manipulation. It opens the door to supply chain attacks. I encourage you to check the Disclosure below to know the WIZ status.
Reversing the firmware deeply (it is really close to the TUYA firmware) should be on my todo-list. ESP and xtensa are interesting subjects...but time is limited.
This smart light chapter is done. I have pwned enough lightbulbs.
More pwn to come...always.
1.8 Disclosure
- 03/11/2018: E-mail to WIZ support asking for contact.
- 04/11/2018: WIZ product manager send an e-mail to me.
- 04/11/2018: I describe the findings in an e-mail (no PGP key of course).
- 06/11/2018: WIZ product manager answers:"We do take security very seriously. At the same time, we have to find solutions that “fit” into what needs to remain a “cheap enough” product for a consumer. Ensuring perfect security when someone has physical access to the product, as in being able to tear it apart, is always a hard thing to do." An other extract from the WIZ manager: "Also, we do not provide easy access to flashing GPIO, no JTAG on our PCBs, not to mention that our lamps are sealed and potted, so it would be quite hard to reflash a product and sell it back looking “new”?"
- 06/11/2018: No more action from my side. They sell sh***y devices and they know that.
- 06/02/2019: Posted.