Pwn the LIFX Mini white
### The Device...
0.1 The Device

LIFX mini White
Bought on Amazon (30 euros).
The lightbulb is plugged. LIFX app is installed on an Android smartphone. Wi-Fi connection is set. The lightbulb works fine.
Wunderbar, easy setup.
0.2 The Teardown
Butcher mode activated:

Classic tools for hardware hacking
Work in progress:
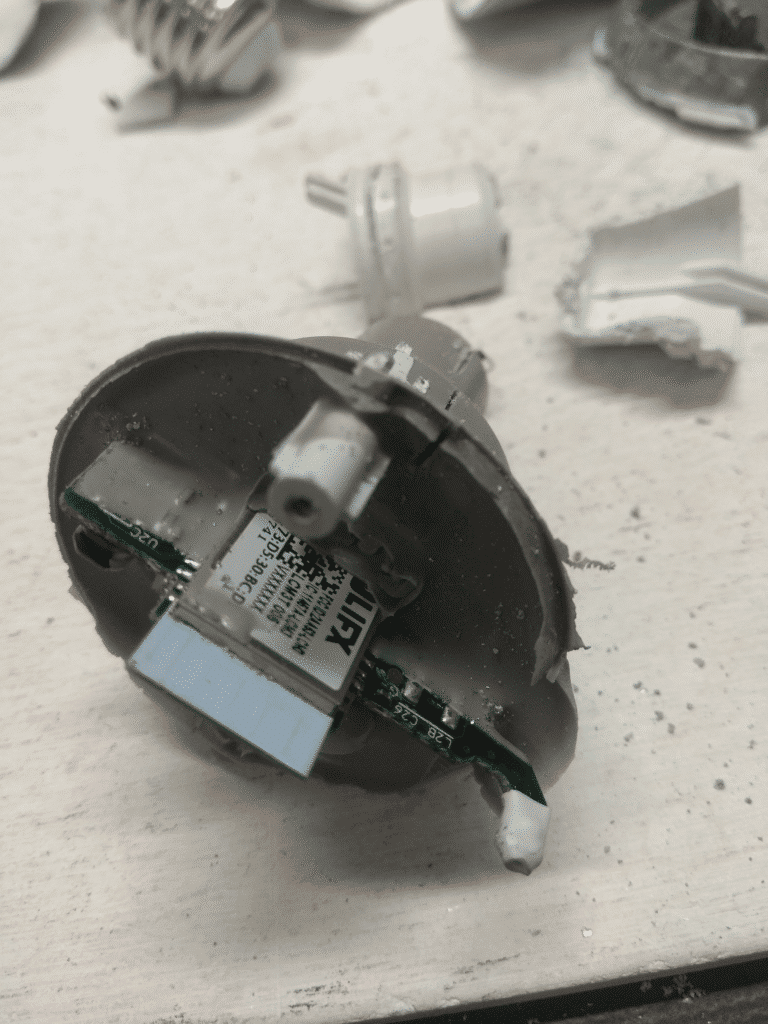
Fireproof paste all around
The most difficult is to clean the board and remove this paste.
0.3 The Setup
The major component of the module is identified as ESP32D0WDQ6, a SoC from ESPRESSIF.
Datasheet is available here.
SDK & Tools are also available on GitHub.
Some pins are soldered to easily connect with a FT2232H board. A little bit of PCB Reverse is needed.
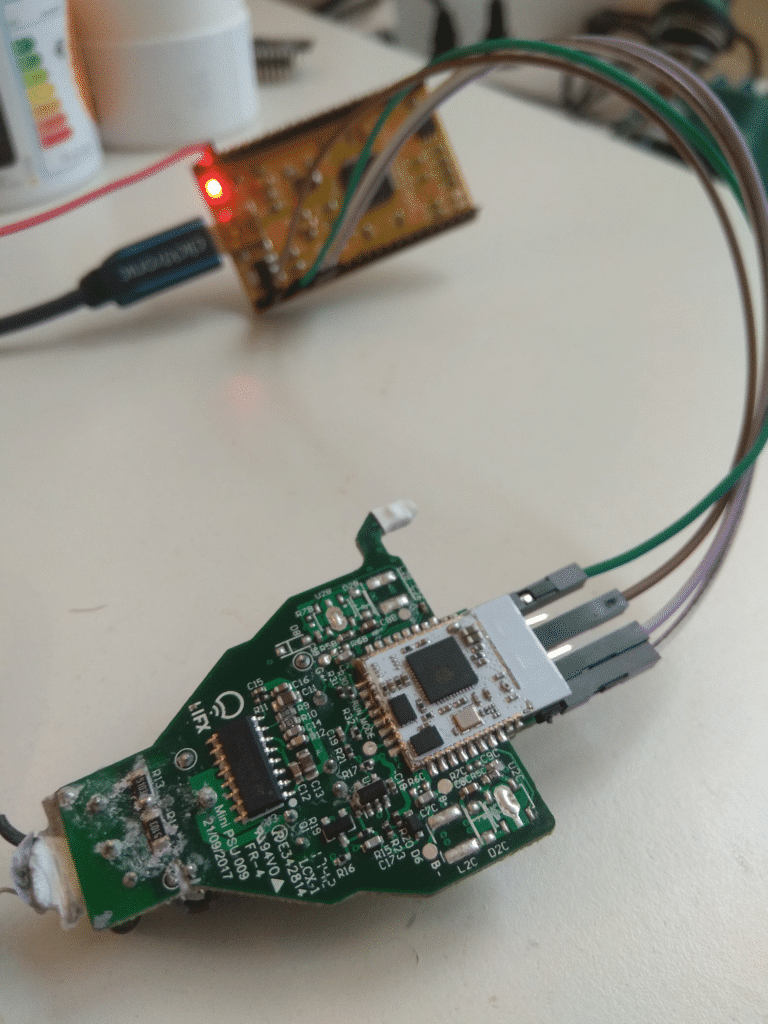
Simple setup
Connections from top to bottom = GND, VCC 3.3V, ADBUS0, ADBUS1.
Once VCC is powered, the LIFX LCM3 is booting:
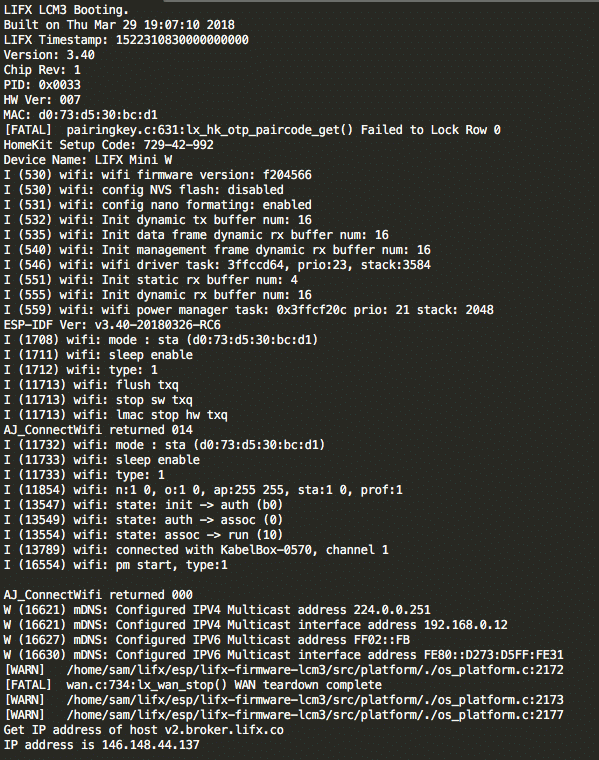
UART activity during boot. It connects directly to the SSID (here KabelBox-0570)
0.4 Vulnerability n*1: Wi-Fi credentials stored in plaintext into the firmware
Dumping the firmware is straightforward. ESP32 is set in Download Mode:

Download mode activated
then launch the read flash command from esp-tool to access the content of the memory:
esptool.py -p /dev/ttyUSB0 -b 460800 read_flash 0 0x200000 flash.bin
A simple research into the binary file flash.bin using an hex editor or even string|grep command is enough to retrieve the Wi-Fi credentials.
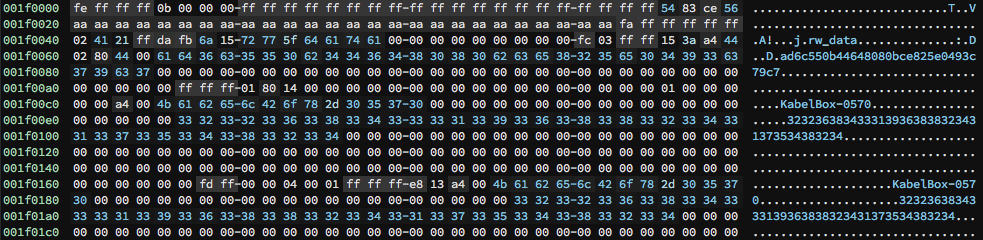
WPA2 key is stored in plaintext (ASCII encoded)
0.5 Vulnerability n*2: No security settings (at all)
To check the device configuration , E-fuses values are dumped:
espefuse.py --port /dev/ttyUSB0 summary
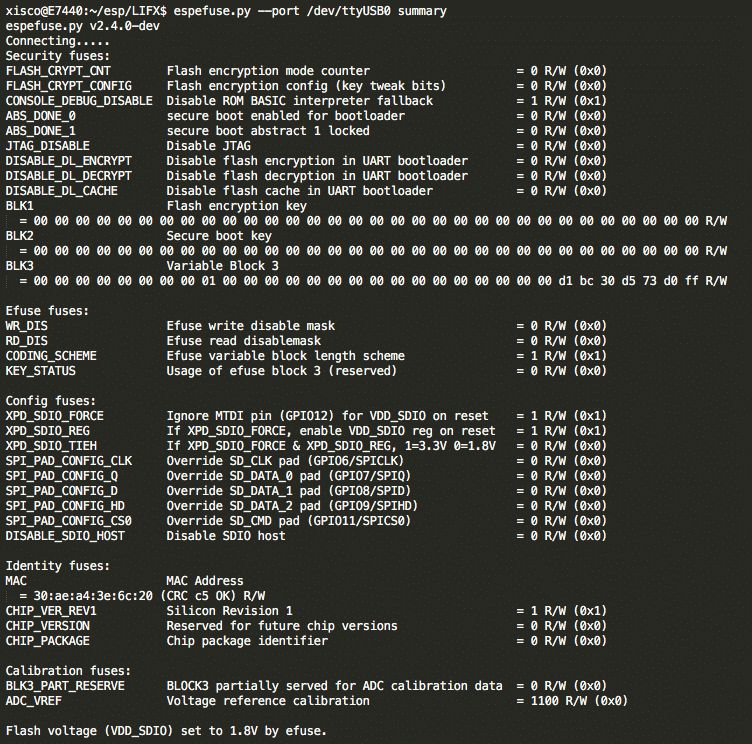
Efuses content
According to the values, this device is totally open (no secure boot, no flash encryption, no JTAG disabled).
0.6 Vulnerability n*3: Root certificate and RSA private key extracted
Root certificate and RSA private key are present into the firmware and are used to connect to LIFX cloud.
Oh Jesus...
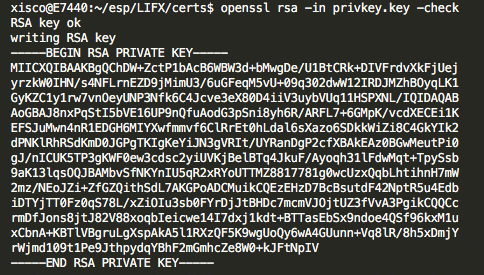
enjoy
I decided to stop the investigation after that.
0.7 Conclusion
In a very short limited amount of time, three vulnerabilities have been discovered:
- Wifi credentials of the user have been recovered (stored in plaintext into the flash memory).
- No security settings. The device is completely open (no secure boot, no debug interface disabled, no flash encryption).
- Root certificate and RSA private key have been extracted.
0.8 Disclosure
- 24/05/2018: E-mail to LIFX. Want to discuss with their engineering team, asking for PGP keys.
- 03/10/2018: No PGP keys, no feedback from LIFX during 4 months. Report finally sent via e-mail.
- 04/10/2018: Acknowledgement from LIFX.
- 17/10/2018: LIFX team confirms the vulnerabilities, asks for a call and a 150 days disclosure.
- 23/10/2018: Call with LIFX team. 90 days disclosure agreement.
- 23/01/2019: Posted.
- 30/01/2019: LIFX statement here.